Citadel Botnet Setup Full Tutorial Guide
Citadel Botnet Setup Full Tutorial Guide with Clean Builder
Today i am going in to introduce new botnet is called CITADEL ZEUS BOTNET its an latest version of ZEUS.

Download Citadel

Contents =
==============
1. Description and facilities.
2. Setting up the server.
2.1. HTTP-server.
2.2. The interpreter PHP.
2.3. MySQL-server.
2.4. Control Panel.
2.4.1. Setting.
2.4.2. Update.
2.4.3. File / system / fsarc.php.
3. Setting Bot.
4. Working with BackConnect.
.
==============================
= 1. Description and facilities. =
==============================
ICE9 - software to steal personal user data from remote systems, Windows. On
plain language of "Troy", "backdoor", "virus". But the author does not like these words, therefore, further documentation
He will call this software "Bot".
Boat is fully based on the WinAPI Interception in UserMode (Ring3), this means that the bot does not use
no drivers or downloads in Ring0. This feature makes it possible to run even from Bota
Guest Account Windows. Plus, it ensures greater stability and adaptability
subsequent versions of Windows.
Bot is developed in Visual C + + version 9.0 +, with no additional libraries are used
Type msvcrt, ATL, MFC, QT, etc. Bot code is written with the following priorities (in descending order):
1. stability (carefully checked all the results of the call functions, etc.)
2. size (to avoid duplication of algorithms, repetitive calls, functions, etc.)
3. speed (not the type of instruction while (1 ){..}, for (int i = 0; i
Functions and features bot:
1. Sniffer traffic for the protocol TCP.
1.1. Interception of FTP logins on any port.
1.2. Interception of POP3 logins on any port.
1.3. The interception of any data from the traffic (a personal request).
2. Intercepting HTTP / HTTPS requests to wininet.dll, ie all programs working with this
library. This includes Internet Explorer (any version), Maxton, etc.
2.1. Substitution ..
3. The functions of the server.
3.1 Socks4/4a/5.
3.2 Bekkonekt for any services (RDP, Socks, FTP, etc.) on the infected machine. You can
access to a computer that is behind a NAT, or, for example, that
banned from the internet connection.
3.3 Getting a screenshot of your screen in real time.
- Do not add ---

- 2.3. MySQL-server. --
----------------------
MySQL is required to store all data on botnete. The recommended version is not lower than 5.1.30, as well
worth considering that when the control panel in the older versions have some
problem. All table control panel, go to a MyISAM, it is important to optimize
speed of work with this format, on the basis of the available server resources.
We recommend the following changes to the MySQL-server setup (my or my.ini):
max_connections = 2000 # Or higher
Download MySQL: http://dev.mysql.com/downloads/
To nix-systems exhibit the right:
. - 777
/ system - 777
/ tmp - 777

ALL FOR EDUCATION PURPOSE ONLY I AM NOT RESPONSE FOR ANY HARM FULL INFECTION OF SYSTEM ETC-
Ardamax Keylogger Tutorial
Ardamax Keylogger Full Step By Step Tutorial
Step 1: Download Ardamax Keylogger
Step 2:
Now, after installing, you will get Ardamax log icon in task bar. Right click on it and select “Enter registrationkey” and make it full version by entering serial key from Serial key.txt file.
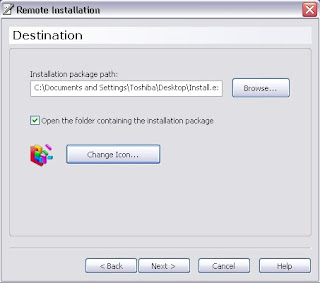
 Step 3: Now, again right click on Ardamax taskbar icon and select “Remote Installation” to see Remote Installation Windows, click Next on it.
Step 3: Now, again right click on Ardamax taskbar icon and select “Remote Installation” to see Remote Installation Windows, click Next on it.
 Step 4:
Step 4:


Click on “Next” to get Appearance screen. Here, click on “Additional components” and untick “Log Viewer” and hit Next.
 Step 5:
Step 5:

Now,on Invisibility screen, check all options and hit Next.

Step 6: Now, on Security screen, click on “Enable” and put the password (remember this pass- you’ll need this later). Check all boxes and hit Next.




Send To : Enter email id to receive keylogs
Username and password: Enter your any Username and pass of email id for sending Keylogs on your email id which yov have mentioned above.
Now hit “Next”.
Step10: In “Control” window dont change anything and hit “Next”.




Note: Your antivirus may detect the downloaded Ardamax keylogger file as virus. Please deactivate your antivirus while installing this Ardamax keylogger. Don’t worry, I never play such cheap pranks of hacking my readers.
















